Introduction
Routing is a fundamental aspect of network infrastructure, directing data packets from their origin to their destination across various network paths. For organizations using FortiGate firewalls, effective routing not only ensures seamless communication across the network but also strengthens security by maintaining control over data flows. This post will describe FortiGate best practise related to the routing. FortiGate’s routing capabilities, supporting both static and dynamic protocols, make it a powerful tool for managing diverse network environments.
Link Health Monitor
Link Health Monitoring is a crucial feature in FortiGate that actively checks the health of links to ensure that data flows through optimal paths. It continuously probes link status by sending health check packets to specified destinations, monitoring connectivity, latency, packet loss, and jitter. If a monitored link fails or falls below acceptable performance standards, the system can automatically switch traffic to an alternative link, ensuring continuity in network operations.
More information you can find at the link.
If FortiGate doesn’t receive replies within the failover threshold, all static routes using the gateway are removed from the routing table.
Link Health Monitor – Configuration
config system link-monitor
edit <name>
set srcintf <interface>
set server <server ip>
set gateway-ip <gateway ip>
set protocol [ping | tcp-echo | udp-echo | twamp | http]
set update-static-route [enable | disable]
next
endset update-static-route→ Remove all routes associated with thesrcintfin the event of an outage.set server→ Use a server IP located beyond the ISP gateway.
Implement Route Failover
- When implementing route failover on FortiGate, it’s crucial to ensure continuous network availability by configuring redundant paths for traffic. Route failover can be achieved using methods like link health monitoring or dynamic routing protocols.
- In dual-ISP scenario is possible to implement ECMP routing. How to implement it you can check at the link.
Routing Design Best Practices
- If you have a multiple path existing for the same network destination, use the distance attribute to ensure only one route is active at a time.
- In case that are you using asymmetric routing, it will disable FortiGate´s stateful inspection.
- Try to summarize host routes to super nets to reduce routing table tables
- Avoid to configure policy routes
- If ECMP routing is not possible to achieve redundancy, use health link monitor
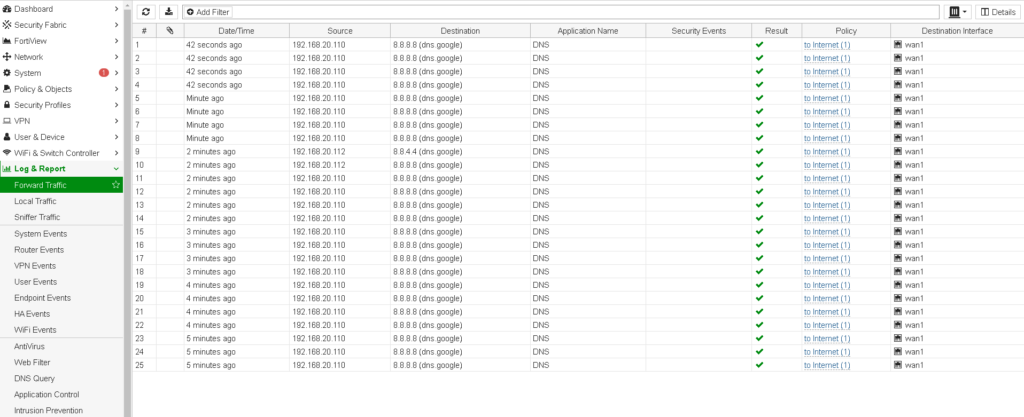
- Under
Log & Report>Forward Trafficuse Destination interface to determine the egress interface for all traffic (in case t
More articles with similar topic:
- FortiGate: Check the Routing Table in the CLI
- FortiGate: Equal Cost Multipath Routing (ECMP) Configuration
- FortiGate: Routing Monitor and Route Attributes
- FortiGate: Static Route Configuration via GUI and CLI