Introduction
In network security, controlling access to open ports is essential for protecting against unauthorized access and reducing attack vectors. FortiGate firewalls offer the flexibility to implement country-based restrictions, a powerful feature that allows administrators to permit or block access from specific geographical locations. This article will guide you through the process of configuring FortiGate to restrict access to open ports based on country, thereby adding another layer of security to your network.
Why Restrict Access by Country?
Restricting access by country can help minimize exposure to threats originating from regions with higher attack rates or to limit access solely to regions where authorized users are based. This configuration can be particularly useful for securing sensitive applications or systems that don’t require global access.
Steps to Configure Country-Based Port Restriction in FortiGate
Step 1: Log into the FortiGate GUI
- Open your web browser and navigate to your FortiGate’s IP address.
- Log in using an account with administrative privileges.
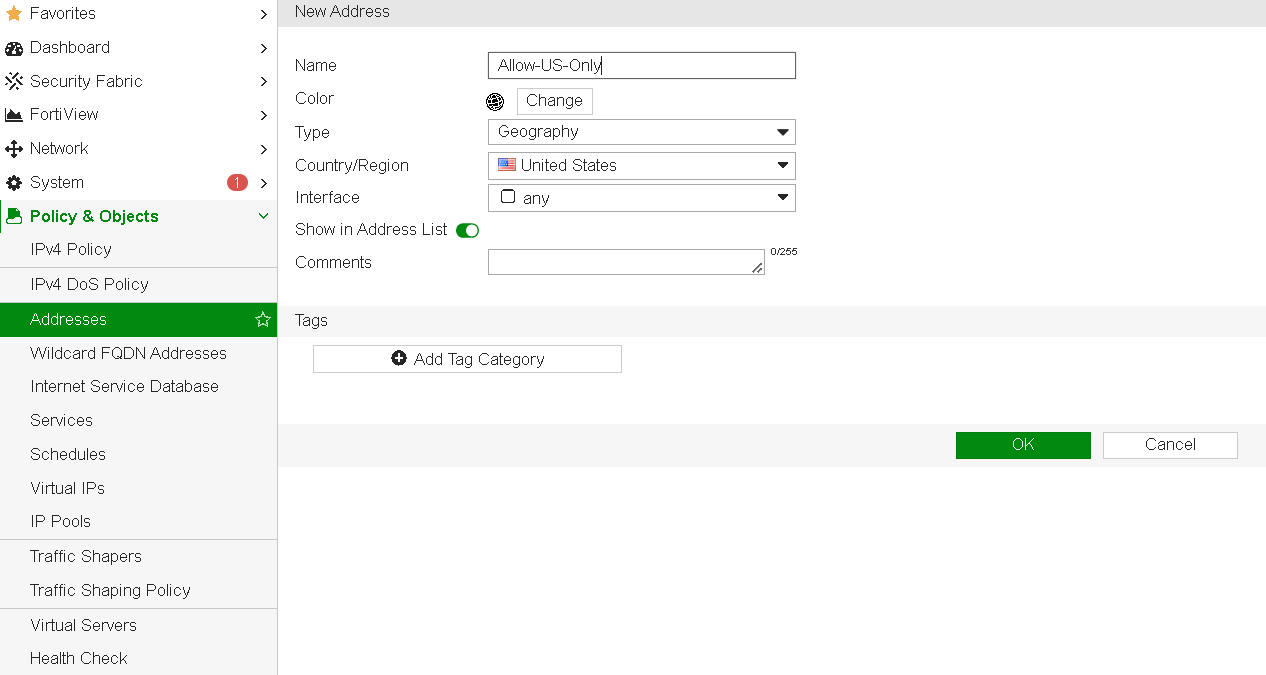
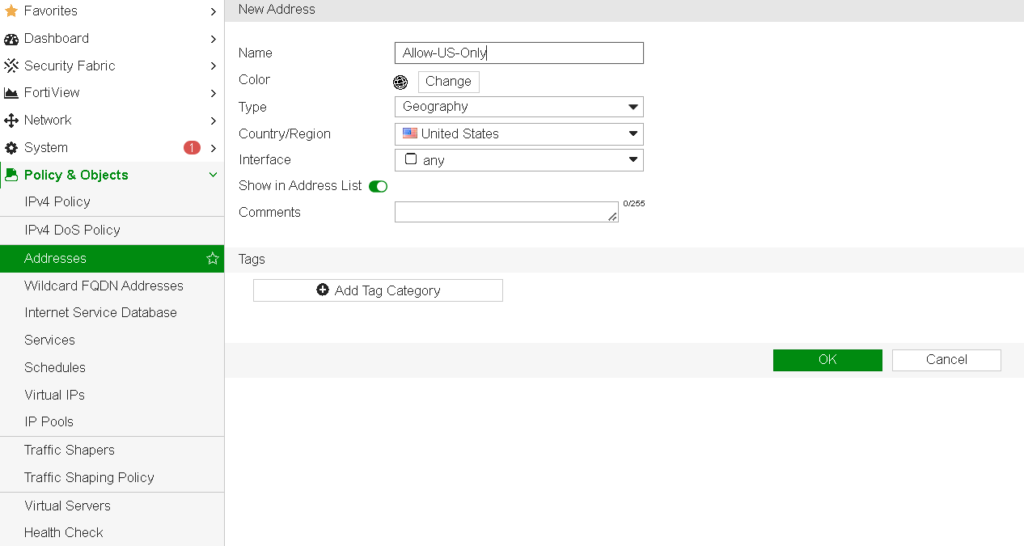
Step 2: Create an Address Object for the Country
- Navigate to Policy & Objects > Addresses.
- Click Create New and select Address.
- Name the address object (e.g., “Allow-US-Only” for allowing access from the U.S.).
- Set the Type to Geography.
- In the Country drop-down menu, select the country you want to allow or block.
- Click OK to save.
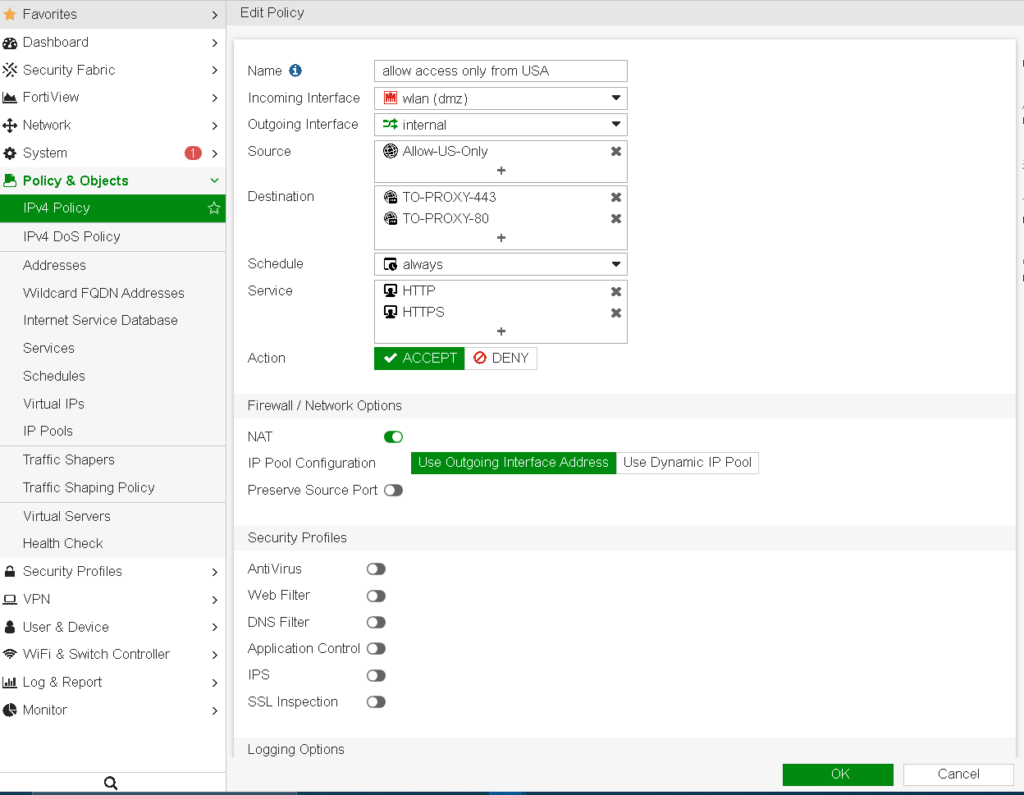
Step 4: Create a Policy to Allow/Restrict Country Access
- Go to Policy & Objects > IPv4 Policy (or IPv6 Policy, depending on your configuration).
- Click Create New to create a new policy rule.
- Set the Incoming Interface to the interface where incoming traffic for the specific port arrives.
- Set the Outgoing Interface to the interface that forwards traffic to your internal network.
- In the Source field, select the address object created in Step 3 (e.g., “Allow-US-Only”).
- For Destination, select the server or IP address hosting the open port.
- Under Service, choose the specific service (port) you want to restrict (e.g., HTTP, HTTPS, SSH).
- Set Action to Accept if allowing only from the selected country, or Deny to block it.
- Configure Logging as needed.
- Click OK to apply the policy.
Step 5: Adjust Policy Order
FortiGate processes policies from top to bottom, so make sure your new policy is positioned appropriately to apply the restriction before any general “allow all” rules.
Step 6: Test the Configuration
After configuring the policy, test the access from the designated country to ensure it works as expected. If you’re restricting access, use tools to simulate connections from different countries to verify the block is functioning correctly.
Additional Tips
- Monitoring Traffic: Use the FortiGate logs under Log & Report > Forward Traffic to monitor attempted connections from different regions.
- Use VPNs for Remote Access: For users who need access from restricted countries, consider setting up a VPN, allowing them secure access while keeping direct access limited.